 icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing.
icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing.
The Open Source Analysis report can be viewed by clicking on the Open Report  icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing.
icon in the CxOSA Project view (top right) regardless of which tab you are currently viewing.
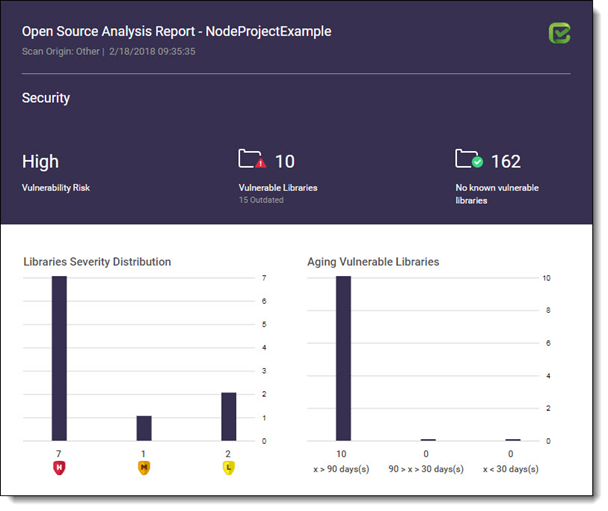
The Open Source Analysis Report indicates the scan origin from which the the analysis was performed. Also includes the time/date stamp indicating the date and time of the last analysis.
Security panel provides information about the distribution of security issues for the project and is divided into the following major categories:
The maximum security severity across all security vulnerabilities found - High, Medium or Low
Distribution of the vulnerable libraries:
Number of libraries without any known security vulnerabilities.
Distribution of the vulnerable libraries by severity. Indicates the number of libraries that have at least one security vulnerability with severity - High, medium or Low.

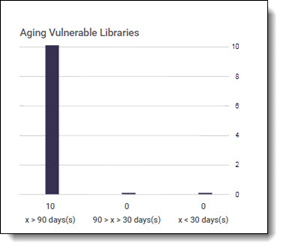
Distribution of vulnerable libraries by timeline:
The Security Vulnerabilities panel provides a list of security vulnerabilities ordered by vulnerability score. The number in parenthesis is the number of vulnerabilities.

The Security Vulnerabilities list includes the following information:
In some cases the CVE reference is not provided for security vulnerabilities. The vulnerability database is based on data from multiple official sources like NVD, Node Security etc. CxOSA detects vulnerabilities by searching the database and only displays a detection if there is a match for specific components or sub-components. This procedure eliminates "false-positive" detection and ensures that the user is only provided with the most accurate and reliable information. Not all security vulnerabilities have a specific CVE reference ID. In these cases we use our own internal identifier. |
The License Risk and Compliance panel provides the distribution of project’s open source libraries by type of license and the level of risk associated with each license.

Distribution of project’s open source libraries by severity
Distribution of project’s open source libraries by type of license, level of risk and occurrence:
A list of outdated libraries with recommendations regarding newer versions available.

The Outdated Libraries list includes the following information:
Possible values are:
Filename Match - with confidence level 70%
Exact Match - with confidence level 100%
A list of libraries with high or medium risk licenses, ordered by license risk score.

The High- Medium Risk Licenses list includes the following information:
 and score level (0 - 100)
and score level (0 - 100) Licensee may use code without restriction
Licensee may use code without restriction Anyone who distributes the code must retain any attributions included in original distribution
Anyone who distributes the code must retain any attributions included in original distribution Anyone who distributes the code must provide certain notices, attributions and/or licensing terms in documentation with the software
Anyone who distributes the code must provide certain notices, attributions and/or licensing terms in documentation with the software Anyone who distributes a modification of the code may be required to make the source code for the modification publicly available at no charge
Anyone who distributes a modification of the code may be required to make the source code for the modification publicly available at no charge Anyone who distributes a modification of the code or a product that is based on or contains part of the code may be required to make publicly available the source code for the product or modification, subject to an exception for software that dynamically links to the original code (e.g. LGPL)
Anyone who distributes a modification of the code or a product that is based on or contains part of the code may be required to make publicly available the source code for the product or modification, subject to an exception for software that dynamically links to the original code (e.g. LGPL) Anyone who distributes a modification of the code or a product that is based on or contains part of the code may be required to make publicly available the source code for the product or modification (e.g. GPL)
Anyone who distributes a modification of the code or a product that is based on or contains part of the code may be required to make publicly available the source code for the product or modification (e.g. GPL) Anyone who develops a product that is based on or contains part of the code, or who modifies the code, may be required to make publicly available the source code for that product or modification if s/he (a) distributes the software or (b) enables others to use the software via hosted or web services (e.g. Affero)
Anyone who develops a product that is based on or contains part of the code, or who modifies the code, may be required to make publicly available the source code for that product or modification if s/he (a) distributes the software or (b) enables others to use the software via hosted or web services (e.g. Affero) and score level (0 - 100)
and score level (0 - 100) Royalty free and no identified patent risks
Royalty free and no identified patent risks Royalty free unless litigated
Royalty free unless litigated No patents granted
No patents granted Specific identified patent risks
Specific identified patent risksA list of policy violated libraries with policy violation, the rule that triggered the policy violation and the policy violation date.

The Policy Violations list includes the following information:
A list of the libraries names and their licenses.

The Inventory list includes the following information:
Possible values are:
Filename Match - with confidence level 70%
Exact Match - with confidence level 100%
If an inventory is marked as "Requires Review", it simply means that the automatic analysis process wasn't able to assign a license to the library. The main reasons for this could be:
Best practice, in this case, is to perform a manual review (please contact Checkmarx support) |
|